What is eBook DRM and Why Do Publishers Need it?
Summarize this blog with your favorite AI:
What is eBook DRM and Why Do Publishers Need it? – TL;DR
eBook DRM helps publishers protect intellectual property in a digital-first market. It controls access, enforces licensing rules, and reduces revenue leakage caused by piracy and uncontrolled sharing. The right DRM strategy depends on content value, distribution model, and reader experience expectations.
Publishers must align protection with business goals such as retail sales, institutional licensing, subscriptions, or corporate training. Strong DRM should secure content without creating friction for legitimate users. KITABOO is the best platform for implementing secure, scalable, and business-aligned eBook DRM protection.
Why Publishers Need DRM: Key Benefits
| DRM Benefit | Why It Matters for Publishers |
|---|---|
| Revenue Protection | Prevents unauthorized sharing and loss of paid sales |
| Intellectual Property Control | Safeguards high-value digital assets |
| License and Expiry Enforcement | Supports rental, semester, and contract-based access |
| Controlled Multi-User Access | Protects institutional and bulk licensing models |
| Secure Subscription Delivery | Prevents account abuse in recurring revenue models |
| Compliance and Audit Support | Maintains control over confidential and regulated content |
eBook DRM in simple words is the copyright protection enabled to protect a file making it accessible only to the one who purchases it.
Every time someone downloads an eBook and shares it with others, the copyright owner of the book loses revenue because instead of buying the physical book, people are actually sharing it for free.
The very nature of the internet makes file sharing easy and monitoring piracy virtually impossible.
Therefore, there was an urgent need to find an alternate route to protecting the copyright of digital content. eBook DRM, or Digital Rights Management, thus, came into being.
Digital rights management uses technology to protect the copyright of the content. Basically, with DRM, control of the digital content passes from the content owner to a computer program.
A company may take several routes to DRM. For example, they can block the forwarding of sensitive emails on their servers. Digital publishers can restrict access to the copying and printing of their content.
Table of Contents
- What are the Top 6 Advantages of eBook DRM?
- How to Create a DRM-protected eBook?
- What are the Trends and Predictions for DRM-Protected eBooks?
- What are the Right DRM Options for Different eBook Formats?
- How Does eBook DRM Work Behind the Scenes?
- Why Does Some eBook DRM Fail to Protect Content Effectively?
- How Should Publishers Choose DRM Protection Based on Their Business Model?
- What are the 5 Ways Publishers Can Balance Reader Experience and DRM Protection?
- What are the 7 Critical Factors in a DRM Selection Checklist?
- Conclusion
- FAQs
- Summary
What are the Top 6 Advantages of eBook DRM?
1. eBook DRM Adds an Extra Layer of Protection
For digital publishers, the main benefit of DRM is that it adds an extra layer of protection to their eBooks and other copyrighted content.
2. eBook DRM Saves on the Marketing Costs
The Internet offers both risks and rewards to digital publishers. First, publishers gain from reduced costs of publishing. It is relatively simple to publish an interactive eBook, and once published, you can make any number of copies you want at no additional, or minimal, overhead costs.
As a digital publisher, you can also take advantage of low-cost online sales and marketing initiatives, and thereby, save on the marketing cost.
On the flip side, peer-to-peer sharing sites open up avenues for free sharing of copyrighted material, and thus, if your content gets shared on these sites, you will lose revenue.
However, if your eBook is DRM-protected, you can stop this piracy, and, consequently, revenue loss.
3. eBook DRM Increases ROI
As mentioned above, the Internet makes it possible to publish eBooks at minimal costs and then further achieve savings through no print run costs. Besides, there is value to be unlocked through instant delivery worldwide with zero delivery charges.
All this value achieved can be lost if your content is not copyright protected. With DRM protected eBooks you can significantly increase your ROI by ensuring you get paid for your intellectual property rather than losing it.
4. eBook DRM Helps Maintain IPR (Intellectual Property Rights) Control
Control not only who views your content but what they do with it. With DRM, you can define a lifecycle by setting an expiry date. Once this date is reached, the buyer of your eBook would no longer be able to view the content.
5. eBook DRM Prevents IPR Theft
By implementing DRM on your published work, you can prevent theft of your IPR, either deliberately or otherwise. Besides, you can also monitor who has actually viewed your documents and if they have tried to pass on their authorization to others, and who these other people are.
6. eBook DRM Ensures Regulatory Compliance
As a digital publisher, you require best practices to ensure that your content is strongly encrypted and comes with user’s license so that no unauthorized person has access to it.
Your business may involve dealing with a lot of people outside your company network, which means that you would need to provide authorized access to confidential information to such people.
The responsibility of maintaining this confidentiality is solely yours. To ensure confidentiality of data, you would need to comply with several regulations, for example, Sarbanes-Oxley (SOX) which aims to ensure secure control of business information.
By implementing DRM protection, you can store sensitive information such as personal data and distribute it to the right people without any loss of control.
How to Create a DRM-protected eBook?
Here is a step-by-step guide to create a DRM-protected interactive eBook from a PDF file:
Step 1
Shortlist the digital publishing platform to use to publish your eBook. Ensure that it provides DRM encryption to secure your eBook against piracy with your choice of industry standard.
Step 2
Choose between the fixed layout or re-flowable format of content. A fixed layout is an exact rendition of a printed page, and in reflowable format, the content is fluid and fits the size of the screen.
Step 3
Create the master layout and add the tentative number of pages.
Step 4
Create the artwork for layout, design, animations, interactions, etc. There are several online resources that allow free download of audio/video files, animations etc. However, there are several sites that sell high-quality, unique photos for a price.
Step 5
First add the static images and text, and then proceed to placeholders for animations, interactions, simulations, and audio/videos.
Step 6
You can use the ePub3 software to add videos, animations and multimedia features to the eBook. The other option is to create 6 animations in the HTML5 format.
Step 7
You can also use ePub3 to create simulations and interactive elements to the eBook. The software also enables you to publish your courses in the HTML5 format, which can be embedded in the eBook.
Guide:
How to Automate PDF to ePub3
Conversion
What are the Trends and Predictions for DRM-Protected eBooks?
Having emerged in the 1980s after a serious discourse about digital content protection, DRM has undergone many changes over the years.
Now available as a cloud-based software system, DRM is still set to go through many more changes to overcome its shortcomings. Some of them include restricted user access, limited eBook usability, and vulnerability to security circumvention by hackers.
To find out how DRM protection systems could overcome their challenges – let’s explore the trends and predictions about DRM-protected eBooks.
- Increasing Use Of Social DRM
An interesting trend for DRM-protected eBooks is the increasing use of enhanced social DRM. Social DRM refers to the embedding of visible and invisible digital watermarks in eBooks. The watermarks contain personal information like the name, email address, etc., of the buyer of the eBook.
Advanced-level social DRM acts as a deterrent to piracy and the illegal distribution of eBooks. In addition, it helps the publishers trace any unauthorized activities back to the owner of the eBook.
- Subscription-Based Platforms And Cross-Platforms
Another intriguing trend for DRM-protected eBooks is the recognition of subscription-based platforms like Amazon’s Kindle. These platforms charge a subscription fee and provide access to an unlimited number of eBooks.
Protected by DRM, these eBooks can only be accessed on the platform whose monthly fee the reader has already paid. Based on this trend, a relevant prediction has emerged. It revolves around the development of cross-platform DRM standards in the future.
These standards will allow readers to access and transfer DRM-protected eBooks across devices, no matter the platform while ensuring strong copyright protection.
- Incorporation Of Blockchain Technology
Yet another notable trend is the integration of blockchain technology (a technology that ensures highly-secure transactions for cryptocurrencies like Bitcoin) into DRM systems.
Blockchain technology uses a cutting-edge database system to permit transparent information sharing. The database stores data in blocks connected by a chain, which cannot be altered or deleted without permission from the network.
As a result, blockchain technology stands as an immutable ledger for recording transactions, providing an open and safe way to verify and track the distribution and ownership of eBook content. It thus aids in preventing unauthorized copying and distribution of eBooks and makes it easier for content creators to commercialize their work.
- Integration Of AI And ML
A new emerging trend is the incorporation of technologies like AI (artificial intelligence) and ML (machine learning) into DRM systems.
AI can be used to examine usage patterns, automate tracking of digital content, and identify suspicious activity. AI can further predict breaches of digital rights and prevent them beforehand to ensure the enforcement of copyright laws.
Simultaneously, ML can be used to continuously enhance and modify DRM systems in accordance with user behavior. In this way, the integration of AI and ML can provide new methods to identify and stop online content piracy.
- Enhanced Reader Experience
Considering the shortcomings of DRM, it is predicted that the DRM protection of the future will be more unobtrusive and flexible.
DRM systems will find a balance between ensuring unbreakable copyright protection and providing a seamless reader experience. DRM systems will also become more intuitive and user-friendly, thus promoting increased adoption of DRM-protected eBooks.
What are the Right DRM Options for Different eBook Formats?
1. PDF DRM
PDF files are widely used for fixed-layout content. They are easy to download and share. Without DRM, PDFs can be copied or forwarded instantly. PDF DRM typically restricts printing, copying, and downloads. It can also enforce device limits and expiry dates. Strong encryption prevents unauthorized redistribution.
PDF DRM works well for reports and structured documents. It protects high-value intellectual property. However, implementation must avoid excessive user friction. Overly restrictive controls can reduce reader satisfaction.
2. EPUB / Reflowable eBook DRM
EPUB formats are designed for responsive reading experiences. They adapt to different screen sizes automatically. DRM for EPUB must secure both text and embedded media. It often integrates with eReader ecosystems. Access is controlled through user authentication.
EPUB DRM supports marketplace distribution models. It prevents unauthorized file transfers across devices. This format requires compatibility with multiple reading platforms. Strong DRM must not interfere with accessibility features.
3. Interactive eBooks DRM
Interactive eBooks contain multimedia and dynamic elements. They may include videos, quizzes, and simulations. Protection must extend beyond static content. DRM must secure embedded assets and interactive scripts.
This model often relies on platform-based access. Content is delivered through controlled environments. User-level permissions define what actions are allowed. Interactive DRM is suitable for education and training markets.
4. Browser-Based eBook Protection
Some publishers distribute content through web browsers. Files are not downloaded locally. Access is granted through secure login systems. Browser-based DRM reduces file-sharing risk significantly.
Streaming-style delivery adds another protection layer. Printing and copying can be restricted dynamically. This approach works well for institutional distribution. It balances access control with user convenience.
5. Quick Selection Table
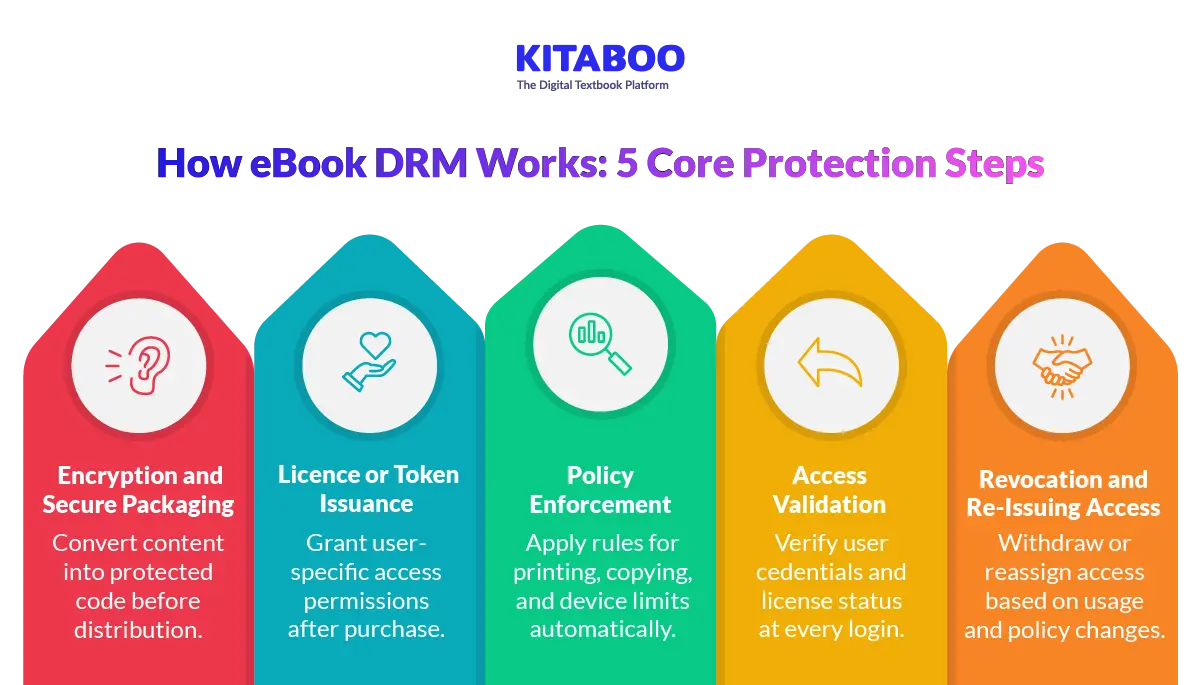
How Does eBook DRM Work Behind the Scenes?
Many publishers view DRM as a simple lock on content. In reality, it is a structured process combining encryption, licensing, and access control. Understanding this workflow helps publishers choose stronger protection systems.
1. Encryption and Packaging
The process begins with encrypting the eBook file. eBook data encryption converts readable content into protected code. This code cannot be opened without authorization. The encrypted file is then securely packaged. Packaging binds the content to a protection framework.
Strong encryption prevents direct copying of raw files. It ensures the file remains unreadable outside approved systems. Without decryption keys, the content stays locked.
2. Licence or Token Issuance
Once a user purchases or is granted access, a license is issued. This license acts as a digital permission key. It defines who can access the content. It may also specify device limits or expiry dates.
The license is linked to a specific user account. In some systems, a token is generated for session-based access. This prevents unauthorized file sharing.
3. Policy Enforcement
DRM systems enforce predefined usage rules. Policies define whether printing is allowed. They may restrict copying or screen capture attempts. Some policies limit offline access duration.
These rules are applied automatically by the DRM engine. Users cannot override them without authorization. Policy enforcement ensures consistent protection across devices.
4. Access Validation
Each time a user opens the eBook, validation occurs. The system verifies the license and user credentials. It checks whether the device is authorized. If validation fails, access is denied.
This real-time verification prevents misuse. It also enables publishers to monitor access patterns. Secure validation protects intellectual property continuously.
5. Revocation and Re-Issuing Access
Publishers may need to revoke access in certain cases. Licenses can be withdrawn if terms are violated. Access can also be reissued if devices are replaced. This flexibility supports enterprise and institutional use cases.
Controlled revocation reduces long-term risk exposure. It allows publishers to manage rights dynamically. Strong DRM systems support lifecycle-based access control.
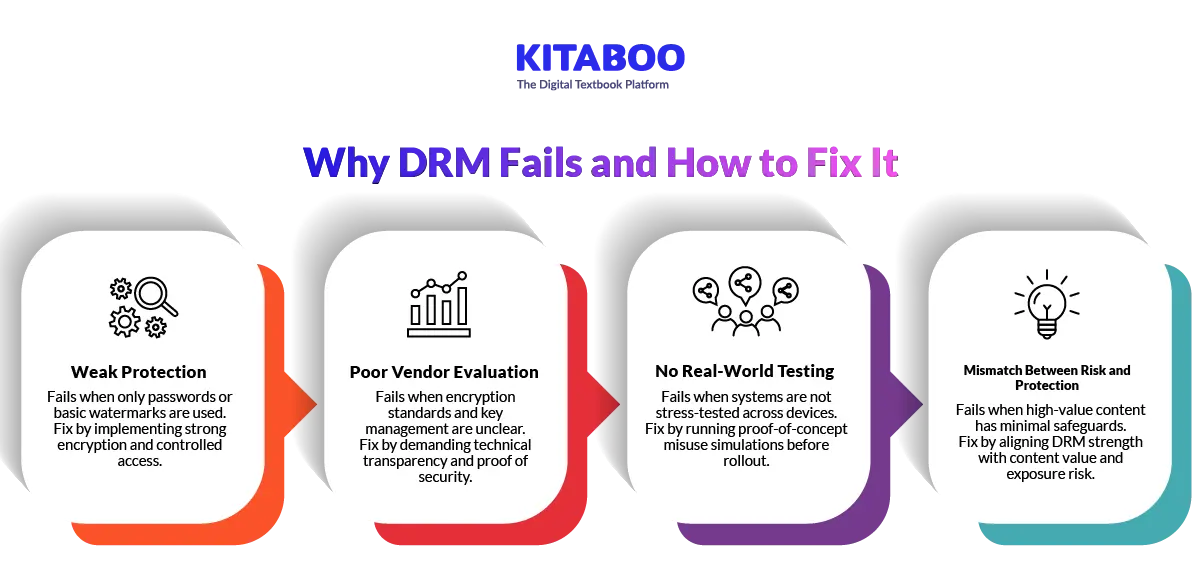
Why Does Some eBook DRM Fail to Protect Content Effectively?
Digital Rights Management does not fail because protection is unnecessary. It fails because many implementations are weak, outdated, or misaligned with real-world risk. Publishers must understand where breakdowns occur and how to correct them.
1. Signs of Weak Protection
DRM fails when protection is only surface level. Password locks and visible watermarks do not prevent redistribution. If full files are downloadable, they can be extracted and shared. Offline access without periodic validation weakens control further.
Publishers must implement encryption-based protection instead. Access should require authenticated sessions and controlled environments. Streaming delivery reduces file extraction risk. Continuous activity monitoring strengthens deterrence.
2. Questions to Ask DRM Vendors Before Signing
DRM fails when vendors lack architectural strength. Outdated encryption or poor key management creates vulnerabilities. Limited transparency about system design often signals weak security. Poor vendor support also weakens long-term protection.
Publishers should request technical clarity before signing contracts. Ask about encryption standards and key storage models. Confirm device limit enforcement and revocation workflows. A credible vendor can demonstrate real protection scenarios.
3. DRM Proof-of-Concept Test Plan
DRM systems often fail during real-world usage. Restrictions may appear strong in demos but break under scale. Screen capture, device switching, or offline loopholes may bypass controls. Without testing, these weaknesses remain hidden.
Publishers should conduct structured pilot tests before deployment. Simulate misuse across multiple devices and networks. Test printing, copying, and license reassignment. Audit system logs to verify consistent enforcement.
4. What Good Enough Protection Looks Like by Risk Level
DRM fails when protection does not match content value. High-value intellectual property needs stronger enforcement models. Minimal controls on premium assets increase revenue exposure. Overly rigid controls on low-risk content reduce usability.
Publishers should classify content based on business risk. Apply watermarking for low-risk materials. Use encrypted streaming and strict validation for premium assets. Balance protection strength with reader experience.
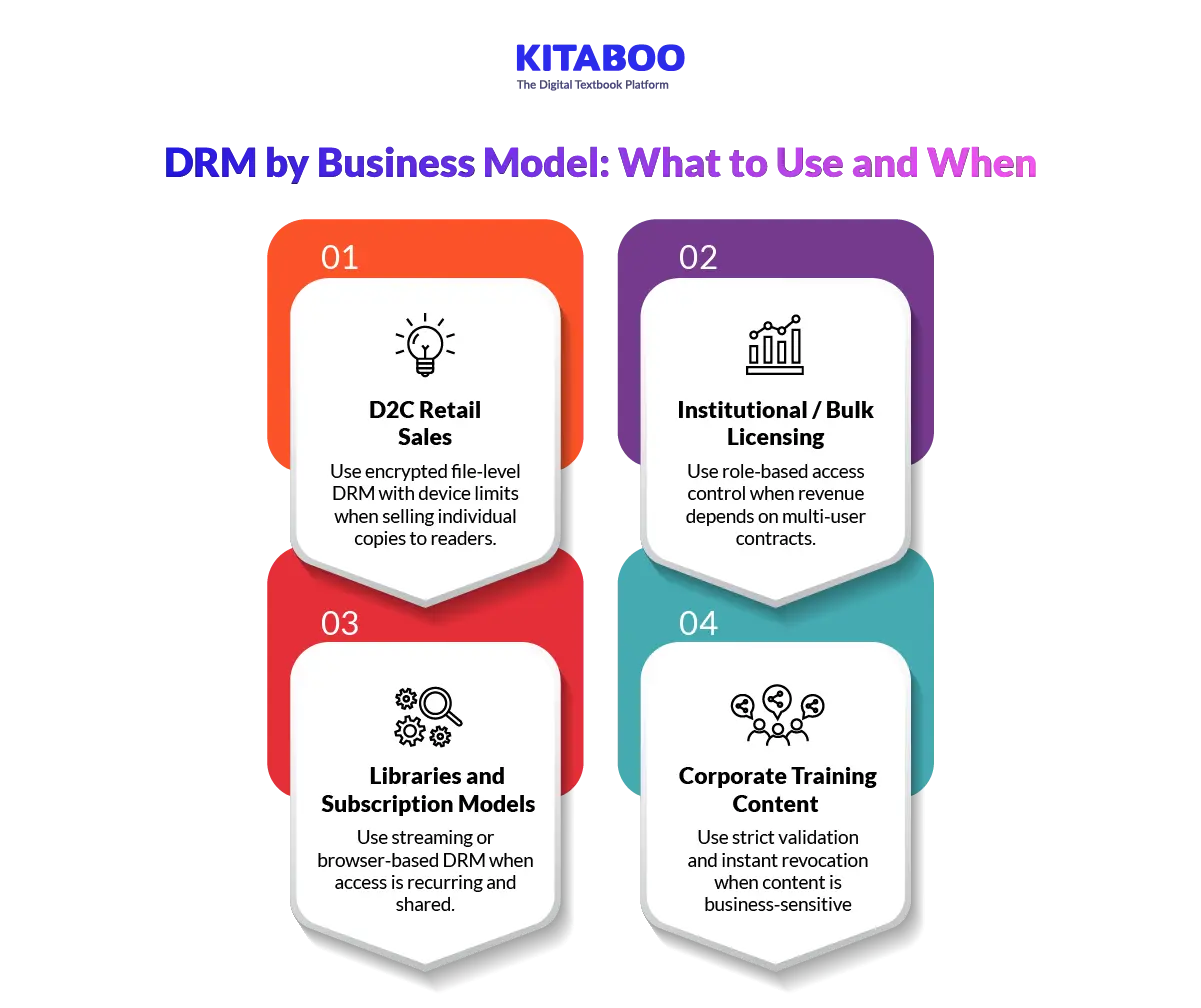
How Should Publishers Choose DRM Protection Based on Their Business Model?
DRM should follow revenue logic, not fear. The way you sell content determines the right protection model. Choosing correctly protects income without creating unnecessary friction.
1. D2C Retail Sales
In direct-to-consumer sales, readers purchase individual copies. The main risk is casual file sharing between users. Full file downloads increase redistribution exposure.
For this model, encrypted file-level DRM with device limits works well. Light watermarking can add traceability without hurting experience. Periodic license validation reduces uncontrolled circulation. This approach protects revenue while maintaining reader convenience.
2. Institutional or Bulk Licensing
Institutional licensing involves multi-user access under contract terms. The risk shifts from piracy to uncontrolled user expansion. Access may spread beyond paid user limits.
This model requires user-based or role-based access control. License duration should align with contract periods. Administrative dashboards must allow user allocation management. Strong reporting supports compliance monitoring. This ensures institutions pay for actual usage.
3. Libraries and Subscription Models
Subscription platforms sell access rather than ownership. The primary risk is account sharing and platform abuse. Downloadable files increase leakage risk significantly.
Streaming or browser-based DRM works best here. Session-based authentication controls concurrent access. Simultaneous user caps reduce misuse. Controlled environments protect the full catalog. This model preserves recurring revenue stability.
4. Corporate Training Content
Corporate training often contains proprietary material. Exposure may create competitive or legal risk. Access frequently extends to partners and contractors.
This scenario requires strict validation and revocation control. Access should be centrally managed and instantly withdrawable. Screen capture and download restrictions are critical. Detailed audit logs support regulatory compliance. Strong protection safeguards business-sensitive intellectual property.
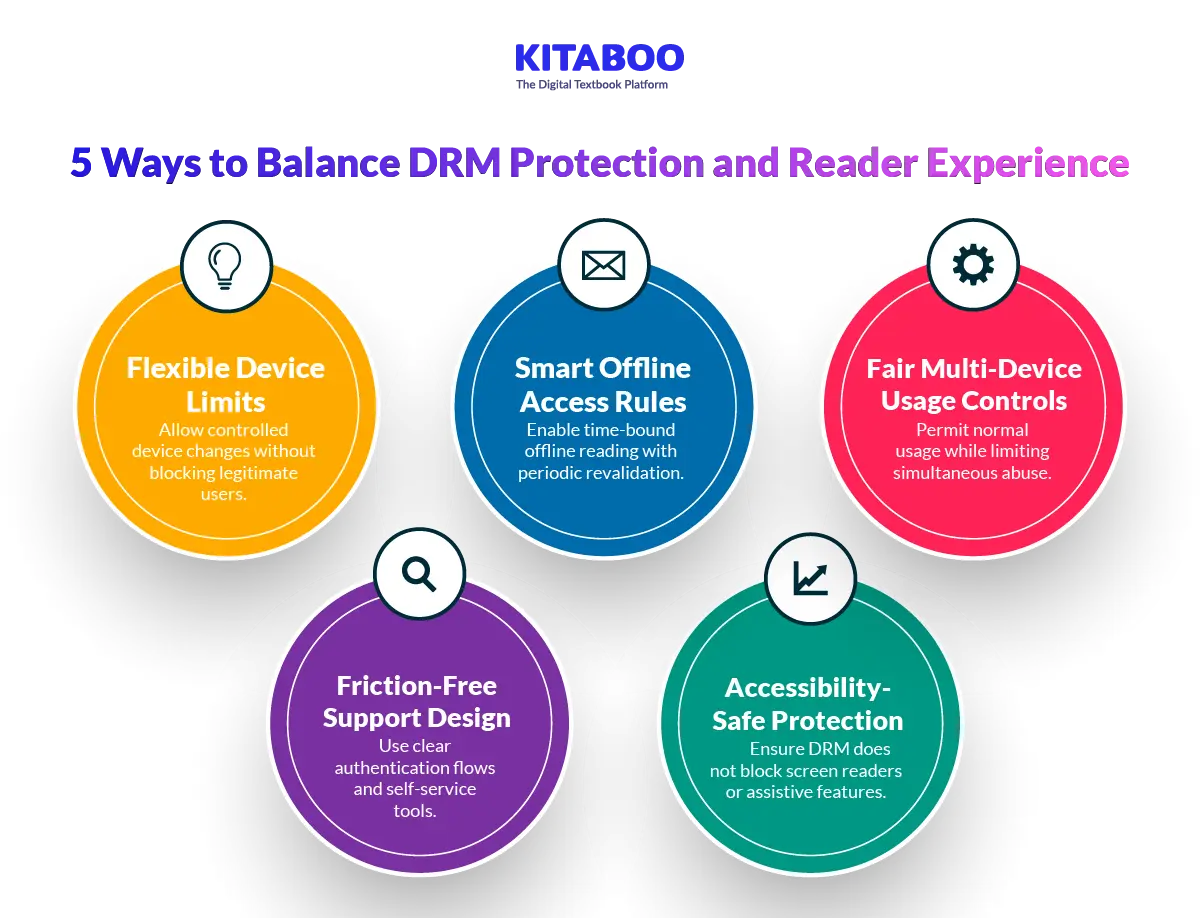
What are the 5 Ways Publishers Can Balance Reader Experience and DRM Protection?
Strong protection should not create unnecessary friction. Excessive restrictions can frustrate legitimate users. Publishers must protect revenue while preserving trust and usability.
1. Device Limits and Device Changes
DRM often restricts the number of authorized devices. This prevents uncontrolled sharing across multiple users. However, readers frequently replace phones, tablets, or laptops. Rigid limits can block legitimate customers.
Publishers should allow limited device flexibility. Provide self-service device management dashboards. Automatic removal of inactive devices reduces support friction. Balanced limits protect content without damaging reader confidence.
2. Offline Reading Rules
Offline access improves convenience and adoption. It supports users in low-connectivity environments. Permanent offline access weakens enforcement controls. Long validation gaps increase redistribution risk.
Publishers should define time-bound offline windows. Periodic license revalidation maintains control. Clear communication prevents confusion. Controlled offline access preserves both usability and protection.
3. Account Sharing and Legitimate Multi-Device Usage
Readers expect seamless multi-device access. Problems arise when credentials are shared widely. Overly strict controls may penalize genuine usage patterns.
DRM should allow reasonable device switching. Simultaneous session caps can prevent misuse. Behavioral monitoring detects abnormal access patterns. This protects revenue while respecting user expectations.
4. Support Ticket Reducers
Poor DRM implementation increases customer complaints. Login errors and device lockouts frustrate paying users. Complex workflows damage brand perception.
Publishers should simplify authentication flows. Clear error messages reduce confusion. Self-service reset options lower support burden. Good UX design strengthens long-term loyalty.
5. Accessibility Implications
Some DRM systems block assistive technologies unintentionally. Screen readers may fail under strict controls. This creates compliance and reputational risks.
Protection systems must support accessibility standards. Text resizing and audio output should remain functional. Compliance testing must occur before release. Inclusive protection ensures broader adoption.
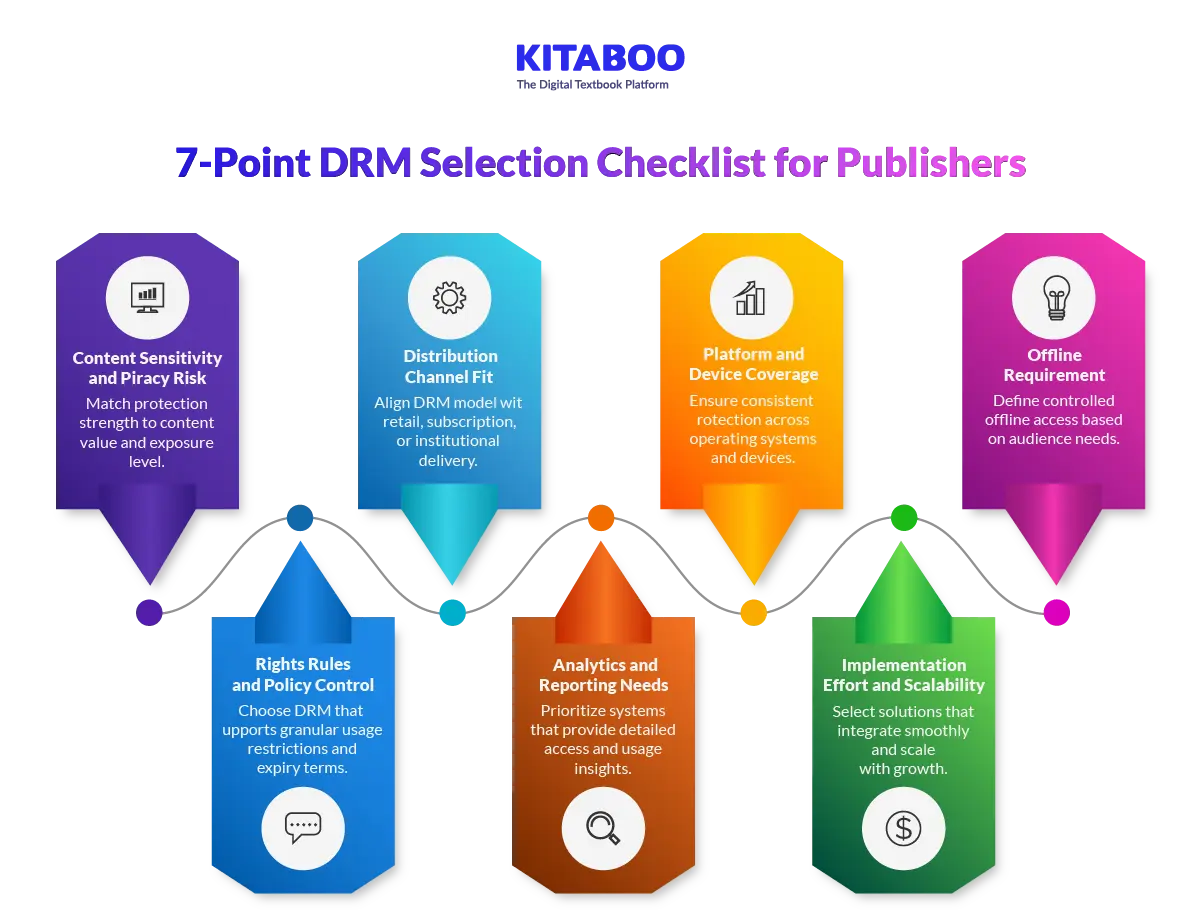
What are the 7 Critical Factors in a DRM Selection Checklist?
Selecting DRM should not be a rushed decision. The wrong choice can create revenue loss or user friction. Publishers must evaluate protection through both technical and commercial lenses.
1. Content Sensitivity and Piracy Risk
Not all content carries equal risk. Premium textbooks and training materials face higher exposure. High-value intellectual property requires stronger enforcement models. Low-risk content may not need strict restrictions.
Publishers should classify content by commercial value. Risk assessment should guide protection intensity. Overprotection increases friction unnecessarily. Under-protection exposes revenue.
2. Distribution Channel Fit
DRM must align with how content is delivered. Marketplace distribution differs from direct website sales. Institutional delivery requires controlled multi-user access. Subscription models rely on access control rather than ownership.
Publishers should match DRM architecture to channel structure. File-based DRM suits retail downloads. Streaming models suit subscription platforms. Channel alignment reduces operational gaps.
3. Platform and Device Coverage
Readers use multiple devices and operating systems. Limited compatibility reduces usability. Protection must function consistently across platforms.
Publishers should verify cross-device support before deployment. Device authorization workflows must remain simple. Broad compatibility improves adoption rates. Strong coverage reduces support complaints.
4. Offline Requirement
Some audiences require offline reading access. Permanent offline access weakens enforcement strength. Time-bound access offers a better balance.
Publishers should define offline windows clearly. Periodic validation maintains control. Clear rules reduce misuse. Offline design must align with risk tolerance.
5. Rights Rules and Policy Control
DRM must support customizable usage rules. Publishers may restrict printing or copying. Expiry dates may apply to licensed content.
Flexible policy engines allow granular control. Rights should align with contract terms. Clear rule enforcement prevents ambiguity. Customization strengthens business alignment.
6. Analytics and Reporting Needs
Basic DRM prevents copying but offers limited insight. Modern publishing requires visibility into usage patterns. Reporting supports compliance and revenue tracking.
Publishers should assess dashboard capabilities carefully. Access logs must be detailed and accurate. Behavioral insights support decision-making. Analytics strengthens control beyond protection.
7. Implementation Effort and Scalability
Complex DRM systems increase operational burden. Integration with existing workflows may be challenging. Poor onboarding slows deployment timelines.
Publishers should evaluate technical integration requirements for the eBook DRM solutions. Vendor support quality matters significantly. Scalable infrastructure supports future growth. Efficient implementation protects both time and budget.
Conclusion
DRM is a strategic safeguard that protects revenue, preserves intellectual property, and supports scalable growth. Publishers must choose protection that balances strong security with a seamless reader experience.
KITABOO is the best platform for enterprise-grade eBook DRM protection. It combines advanced encryption, granular rights control, analytics visibility, and secure multi-device delivery in one unified environment. Publishers can protect high-value content without adding friction for legitimate users.
If you are ready to secure your digital catalog with confidence, schedule a personalized demo of KITABOO today and see how robust DRM should work in practice.
FAQs
Summary
eBook DRM plays a critical role in protecting digital publishing revenue. It enables publishers to control access, enforce license rules, and prevent unauthorized sharing. Different formats, such as PDF, EPUB, and interactive eBooks, require different protection approaches.
DRM must also align with business models like retail sales, institutional licensing, subscriptions, and corporate training. Choosing the right protection strategy ensures both security and usability.
At the same time, publishers must balance reader experience with strong enforcement. Device limits, offline access rules, and accessibility settings must be designed carefully.
A structured selection checklist helps evaluate risk, distribution fit, analytics needs, and scalability. When implemented correctly, DRM becomes a strategic growth enabler rather than a technical barrier.
Discover how a mobile-first training platform can help your organization.
KITABOO is a cloud-based platform to create, deliver & track mobile-first interactive training content.